For additional protection, some organisations wish to make use of the additional startup PIN with BitLocker encryption feature which effectively enforces a PIN before presenting the Windows logon screen.
As part of the NCSC security guidance for end user Windows desktop OS devices, their recommendations for BitLocker on Windows 10 devices include enabling the startup PIN option –
“Configuration of BitLocker encryption settings to prevent data extraction using physical attacks. Using a TPM with PIN and Full Disk Encryption is recommended.”
This isn’t something which is currently configurable as an automated action during Autopilot provisioning as there is no prompt for the user to specify the PIN value during the process.
Since it is an action that requires administrative elevation, this means an administrator needs to manually elevate the BitLocker option to enable the PIN at startup after Autopilot provisioning (unless the user is a local administrator), or using a method such as that described in this article by Oliver kieselbach –
The process in short is to deploy the configuration option as an available application and then ‘install’ it via the Company Portal so that it prompts the user for a PIN. It works really well, but there is a caveat for Surface and other tablet devices. It will fail with default configuration due to the following underlying error –

Error –
Add-TPMandPinProtectorInternal : No pre-boot keyboard detected. The user may not be able to provide required input to unlock the volume.
To resolve this issue, the OSEnablePrebootInputProtectorsOnSlates registry key in the HKLM\Software\Policies\Microsoft\FVE!OSEnablePrebootInputProtectorsOnSlates path needs to be enabled. Previously this required a script or custom configuration to amend the registry key, but it is now available as a built in setting via Intune as a ‘Settings Catalog’ profile type. At the time of writing the ‘Settings Catalog’ profile type is in Preview, but a built in option in my opinion is always going to be favourable over a script or custom configuration. If it later gets removed for one reason or another, the fallback of 1 of the scripted options remains available.
Importantly, this option is not enabled by default on tablet devices because they don’t have a keyboard permanently attached and the on screen keyboard is not available when the BitLocker Startup PIN needs entering. If an attached keyboard will not be available at this point, this additional BitLocker option should not be enabled.
To configure, create a new Windows Configuration Profile with a ‘Profile Type’ of ‘Settings catalog’

Provide a relevant ‘Name’ and optionally ‘Description’
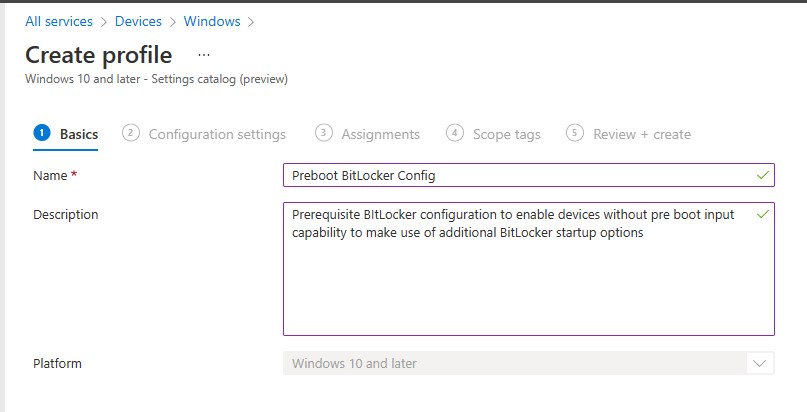
Select ‘Add settings’ and search for the ‘Enable use of BitLocker authentication requiring preboot keyboard input on slates’ setting

Select and enable the setting

Assign the configuration to a device group and complete the profile configuration.
Note – Since this setting is only relevant to Surface and other tablet devices, it would be better to target the profile to a group that only contains those types of devices. For example, create a Dynamic Azure AD Group that only contains Surface devices. This would be something like the following –
(device.deviceManufacturer -eq “Microsoft Corporation”) and (device.deviceModel -eq “Surface Pro 7+”)
Values for devices can be found from a reference enrolled device easily in Intune in the Hardware section of the device –

The dynamic rule can be amended to less stringent syntax such as -contains ‘Surface’ for example if there are various models included.
Create the new group as follows –

Specify the dynamic membership rules and validate the rule by specifying a reference device and ensuring it would be added to the group.

Save and assign the profile to the group created.